Connect with safety – secure data explained
With the amount of data carried in today’s cars – much of it travelling outside the vehicle – it’s imperative to ensure secure connections are maintained. Dave Moss reports.
ccording to predictions from business information provider IHS Markit, by 2022, 87% of all US vehicles will be telematics-equipped, along with 91% in Germany and 92% in the UK. The following year, worldwide connected car sales will reach 72.5 million units, when around 70% of all new light vehicles will include some form of factory-installed telematics.
Hybrid telematic systems with a dongle or mobile phone internet link are expected to be the biggest growth driver, though in-car use of smartphones, tablets and laptops connected via everything from car wi-fi to USB ports will play a big part.
“A large proportion of vehicles already feature multiple connections, especially in the luxury segment,” says Anna Buettner, automotive infotainment manager at IHS Markit. “This trend is expected to spread to lower segments in coming years, as strong market demand brings connectivity to vehicles and regions that have traditionally lagged behind.”
The move towards telematics is being driven by demand for flexible phone and infotainment facilities – part of an electronic revolution as numbers of largely hidden computers controlling internal car systems have soared. Cars and computers have existed happily together for many years, but Ron Plesco, a principal in KPMG’s cyber security practice, believes car internet connections bring ever-growing risks.
“A car fitted with vehicle-to-vehicle, vehicle-to-infrastructure, cellular, Bluetooth and wi-fi connections, for example, has a much greater attack surface than one with only a single, isolated computer system,” he says.
“In fact, recently, a malware attack was identified that could put 5.3 billion devices with Bluetooth signals at risk.”
Hack-proof hopes
The importance of securing company and personal computers from hacking and virus infection is widely known. For years, similar risks to car computer systems were hardly mentioned, but as cars have moved on from single wired diagnostic ports, hacker access has become easier and problems more intense.
“I do think there was a certain lack of awareness of the security implications of, say, using wireless connection to communicate Tyre Pressure Monitoring System (TPMS) data,” says Intertrust Secure Systems’ vice president and general manager, Bill Horne. “It’s a general problem with security that often the functionality and cost savings are so compelling that little thought goes into possible security implications, especially in industries where it’s never been a problem before. Who would have thought that TPMS would be a vector for attack?
“Hackers are incredibly talented at finding clever ways to exploit vulnerabilities and finding paths through multiple components to achieve an end goal,” adds Horne. “Safety is naturally the biggest concern – anything putting lives at risk needs to be taken very seriously. From a security perspective, you have to think of the entire threat model. What are the threats, to confidentiality, integrity and availability? Getting into a low-risk component can be a stepping stone to attacking more safety-critical components – or other computers – even your mobile phone.”
George de Boer, leader of connected car initiatives at TomTom Telematics, agrees, while pointing to wider issues. “If you want to secure the connectivity of vehicles, regardless of aftermarket or line-fitted connectivity, you have to look at the complete chain and all the different vectors,” he says. “A vector could be the wireless connection, but also includes the interfaces of devices in the car – and how access codes are given to employees that maintain systems in the cloud.”
The threat of infiltration
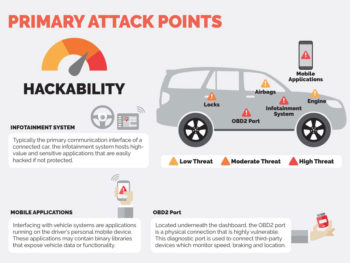 Fleet telematics systems could also be a security risk, especially where internet connection is via a dongle or mobile phone and GPS-based vehicle tracking is incorporated, or there’s a link to other connected car functions. The implications of hacking into fleet vehicles are wide-ranging and with more and more connected cars entering service, there are big questions about how serious the security issues actually are. De Boer has no doubt – and sees some related problems.
Fleet telematics systems could also be a security risk, especially where internet connection is via a dongle or mobile phone and GPS-based vehicle tracking is incorporated, or there’s a link to other connected car functions. The implications of hacking into fleet vehicles are wide-ranging and with more and more connected cars entering service, there are big questions about how serious the security issues actually are. De Boer has no doubt – and sees some related problems.
“The threat is real – plenty of cases from the recent past demonstrate that,” he says. “And these problems will only become more frequent as more cars become connected. Related security topics are also growing, not only for aftermarket telematics systems – but also for car manufacturers. But next to security, there are also risks associated with data privacy, and negative PR.”
Plesco believes security issues shouldn’t be underestimated: “Simply stated, the threats are very current, and present a clear and present danger,” he says. “But consider – from a hacker’s perspective – the potential payoff of cyber-attacking not one car, but a hundred, or a million. With the connectivity that’s out there today, and the broadcast reach of the internet, the same attack technique that works on a single car can be applied to all internet-connected cars – with relative ease.”
Reducing risk means being constantly on guard, according to Horne: “Essentially, you have to maintain good security hygiene, as you would for home and business computers.” he advises. “Patch and update systems regularly, by keeping vehicles on regular service schedules. Only connect wi-fi or Bluetooth to trusted devices and, as things such as installable apps become more popular, only download from reputable sources.”
Control your data
Unauthorised access to fleet telematics systems could mean leakage of confidential driver, client or company data – and possible interference with internal company networks. De Boer believes these risks deserve special thought. “No system will be 100% secure, just as no bank is impossible to break into,” he says. “The questions should be how much is being done to secure the solution and how is data being kept private? Fleet and mobility managers should ask suppliers how they ensure security is part of their design process, their fabrication and their lifecycle management. Those concerned about data privacy should ask suppliers if it’s possible to limit data collection to particular pre-defined goals, and about ways to limit accessibility to certain data. Secure and private systems are possible, but take significant effort. Ensuring they remain so is an ongoing process, which also means the right systems don’t come at the lowest price.”
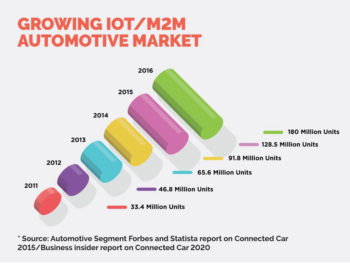 In recent years enough evidence has surfaced to suggest that many early connected vehicle systems – including fleet telematics – were less than ideally secure, but lessons are being learned. Around the world, governments, manufacturers and certification organisations are leading efforts to address the challenge. Stricter manufacturing guidelines are emerging, increasingly built on security best practices from other branches of electronics. In 2015 the US auto industry recognised the issues by establishing an ‘Information Sharing and Analysis Center’, to share intelligence on car electronics and vehicle data network vulnerabilities. The Association of Global Automakers has also recently introduced ‘Privacy Principles for Vehicle Technologies and Services’ documentation.
In recent years enough evidence has surfaced to suggest that many early connected vehicle systems – including fleet telematics – were less than ideally secure, but lessons are being learned. Around the world, governments, manufacturers and certification organisations are leading efforts to address the challenge. Stricter manufacturing guidelines are emerging, increasingly built on security best practices from other branches of electronics. In 2015 the US auto industry recognised the issues by establishing an ‘Information Sharing and Analysis Center’, to share intelligence on car electronics and vehicle data network vulnerabilities. The Association of Global Automakers has also recently introduced ‘Privacy Principles for Vehicle Technologies and Services’ documentation.
Plesco expects a very different approach to connected vehicle security in future: “OEMs and the supply chain have begun taking the threat more seriously and are even considering cybersecurity as a market differentiator,” he says. “We’ve entered a new era in the automotive industry, propelled by massive technological and business model change. Protecting the fleet will require carmakers to actively maintain connectivity and provide real-time security support to embedded software – on millions of vehicles. That’s a significant shift in the traditional operating model, where problems are dealt with using recalls and dealer networks do most of the work.”
De-fleeting needs data deleting
Connected car security issues can spread well beyond one vehicle, with stories continuing to surface over difficulties in permanently releasing external equipment connections. Full memory clearance before computer, tablet and smartphone disposal is an established routine in most companies, and similar procedures should be followed on disposal of vehicles, including removal of phone pairing, and ensuring all ‘connected car’ external links are broken.
However this may not always be straightforward, varying widely depending on the vehicle manufacturer. Reports have emerged – seemingly mostly involving premium marques – of partial links remaining, allowing first owners to remotely operate functions and track their previous vehicle’s location, sometimes long after sale. In some cases it’s been claimed manufacturer intervention has been required to complete the process.
When vehicles are being de-fleeted, a master data clearance is recommended before vehicle handover – to avoid any future data privacy and vehicle security issues.
Connected cars demand new solutions for new threats
With the coming of the ‘connected car,’ the risk of personal, company or vehicle data being stolen or compromised is higher than ever before. Any internet-connected device may provide vehicle system access for hackers, and it’s not just one car at risk – it could be many of the same make or model.
Ron Plesco believes manufacturers must deal with these new problems and new threats in entirely new ways: “Managing the risk of a fleet-wide cyber attack will demand that companies throughout the automotive ecosystem take a new approach, especially with regulators, customers, and suppliers expecting car brands to maintain responsibility for both quality and safety, as has historically been the case,” he says. “The industry will need to transform many aspects of the business, including how companies develop, service, and support vehicle networks – and the assets, capabilities, people, and the relationships they prioritise.”
Source: https://internationalfleetworld.com
FLEET MANAGEMENT AUDIT
Fleet management is the use of a set of vehicles in order to provide services to a third-party, or to perform a task for our organization, in the most efficient and productive manner with a determined level of service and cost.
Fleet management activities are shown in the following graph 1:

Graph 1: fleet management activities
The proposal audit analyses and assesses all fleet management activities shown in the graph 1, and its main goals are:
- Know the overall status of the fleet management activities
- Provide the analysis, the assessment, the advice, the suggestions and the actions to take in order to cut costs and increase the efficiency and efficacy of the fleet management activities
With the information obtained, we’ll elaborate a report that holds the overall status of the fleet management as well as the suggestions, recommendations and the measures to take in order to cut costs and optimize the fleet management activities.
CLICK ON THE FOLLOWING LINK TO DOWNLOAD THE PROPOSED FLEET MANAGEMENT AUDIT:
Fleet Management Audit AFMC
Contact:
José Miguel Fernández Gómez
34 678254874
info@advancedfleetmanagementconsulting.com



